The financial world stands at a crossroads. For centuries, our economic systems have operated on a fundamental assumption: trust must be centralized, managed, and enforced by authorities. But Bitcoin introduced a radical alternative—a system where trust isn’t given blindly but earned through verification, transparency, and mathematical certainty. This paradigm shift challenges not just how we transfer value, but how institutions safeguard it.
As digital assets move from the fringes to the mainstream, traditional custody models are proving inadequate for this new asset class. The unique properties of cryptocurrencies demand new approaches to security, verification, and trust—approaches that often run counter to established financial practices but align perfectly with open source principles.
Centralized vs. Decentralized Trust: A Fundamental Paradigm Shift
The Trust Paradigm Shift: From centralized authority to distributed verification
Traditional finance operates on a centralized trust model where authority flows from the top down. Banks, clearinghouses, and regulators serve as trusted intermediaries, with customers placing faith in these institutions to act honestly and competently. This model has persisted for centuries, creating a financial system where trust is delegated rather than verified.
Bitcoin introduced a revolutionary alternative captured in its unofficial motto: “Don’t Trust, Verify.” This approach inverts the traditional model by eliminating the need for trusted third parties. Instead, it creates a system where:
Traditional Finance Trust Model
- Relies on centralized authorities (banks, regulators)
- Trust is assumed within institutional boundaries
- Verification happens through audits and regulatory oversight
- Security through restricted access and confidentiality
- Limited transparency with selective disclosure
Bitcoin’s “Don’t Trust, Verify” Model
- Distributes trust across a decentralized network
- Trust is earned through cryptographic proof
- Verification happens in real-time by all network participants
- Security through transparency and consensus
- Complete transparency with public ledger verification
This paradigm shift extends beyond simple transactions to fundamentally challenge how we think about custody. In traditional finance, assets are secured by creating barriers—vaults, guards, and restricted access. In Bitcoin’s model, security emerges from transparency, where anyone can verify but no single entity can control.
“The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous.”
This fundamental difference creates a new foundation for institutional custody—one where security doesn’t depend on blind trust in a provider but on verifiable processes and transparent systems.
Understand the Trust Paradigm Shift
Download our comprehensive guide to Bitcoin’s verification model and how it’s transforming institutional approaches to digital asset security.
The Institutional Custody Imperative: Why Traditional Models Fall Short
Institutional investors face unique challenges when securing digital assets that traditional custody models simply weren’t designed to address. The fundamental properties of cryptocurrencies—bearer instruments secured by private keys with irreversible transactions—create security requirements that differ dramatically from traditional assets.

Key Challenges in Digital Asset Custody
Traditional custody solutions typically rely on a simple model: the custodian takes possession of assets and becomes responsible for their safekeeping. This model breaks down with digital assets for several critical reasons:
Traditional Custody Strengths
- Established regulatory frameworks
- Familiar operational processes
- Integration with existing systems
- Clear liability and insurance models
Digital Asset Custody Challenges
- Private key vulnerability to theft or loss
- Irreversible transactions with no recourse
- Complex technical requirements
- Evolving regulatory landscape
- Need for both hot and cold storage solutions
Regulatory Hurdles and Operational Complexities
Institutions face a complex regulatory landscape when implementing digital asset custody solutions. Requirements vary by jurisdiction, with some regions requiring specific licenses for crypto custody while others have yet to establish clear frameworks. This regulatory uncertainty compounds the technical challenges of securing digital assets.
Operationally, institutions must develop entirely new processes for:
- Key generation ceremonies with proper entropy and security
- Secure backup procedures that don’t create single points of failure
- Transaction signing workflows with appropriate controls
- Integration with existing portfolio management systems
- Audit and compliance reporting specific to digital assets
These challenges highlight why traditional custody models are fundamentally inadequate for digital assets. The solution isn’t simply to adapt old models but to embrace the paradigm shift that Bitcoin introduced—moving from delegated trust to verified security.
According to a 2023 survey by the Global Digital Asset Custody Association, 78% of institutional investors cited security concerns as their primary barrier to digital asset adoption, with regulatory uncertainty (65%) and operational complexity (57%) following closely behind.
Open Source as the Foundation of Trust
The open source movement shares a philosophical foundation with Bitcoin’s “Don’t Trust, Verify” ethos. Both reject the notion that security comes from obscurity and instead embrace transparency as the path to trustworthiness. This alignment makes open source principles particularly valuable for institutional custody solutions.

The Core Principles of Open Source Security
Transparency
Open source code can be inspected by anyone, eliminating hidden vulnerabilities and backdoors. This transparency creates accountability and allows institutions to verify exactly how their custody solutions work.
Peer Review
Open source projects benefit from diverse scrutiny, with experts from around the world examining code for flaws. This collective intelligence typically identifies vulnerabilities faster than closed-source security teams.
Collaborative Development
The ability for multiple parties to contribute improvements creates more robust solutions. Institutions can adapt and enhance custody systems to meet their specific requirements.
Real-World Examples of Open Source Security Success
The effectiveness of open source security isn’t theoretical—it’s demonstrated through numerous examples where transparency has enhanced security:
| Vulnerability | Discovery Method | Resolution Time | Impact |
| Heartbleed (OpenSSL) | Independent security researcher | Fixed within days of public disclosure | Affected ~17% of secure web servers globally |
| Bitcoin Value Overflow (2010) | Community member on Bitcoin forum | Patched within hours | Could have created infinite Bitcoin supply |
| Spectre/Meltdown | Academic researchers + industry collaboration | Coordinated response across ecosystem | Affected virtually all modern processors |
These examples demonstrate how open source security practices can identify and address even the most critical vulnerabilities. For institutional custody, this approach creates a foundation where security doesn’t depend on blind trust in vendors but on verifiable, transparent systems.
“Given enough eyeballs, all bugs are shallow.”
The open source approach to security aligns perfectly with the needs of institutional investors who require certainty about how their digital assets are secured. Rather than trusting vendor claims, they can verify the security of their custody solutions directly or through independent auditors.
Stay Updated on Open Source Security
Subscribe to our newsletter for the latest developments in open source custody solutions and security best practices.
Practical Applications: Open Source in Institutional Custody
The theoretical benefits of open source are being realized through practical custody solutions that leverage transparency and verification to create institutional-grade security. These solutions demonstrate how the trust paradigm shift is transforming from concept to implementation.
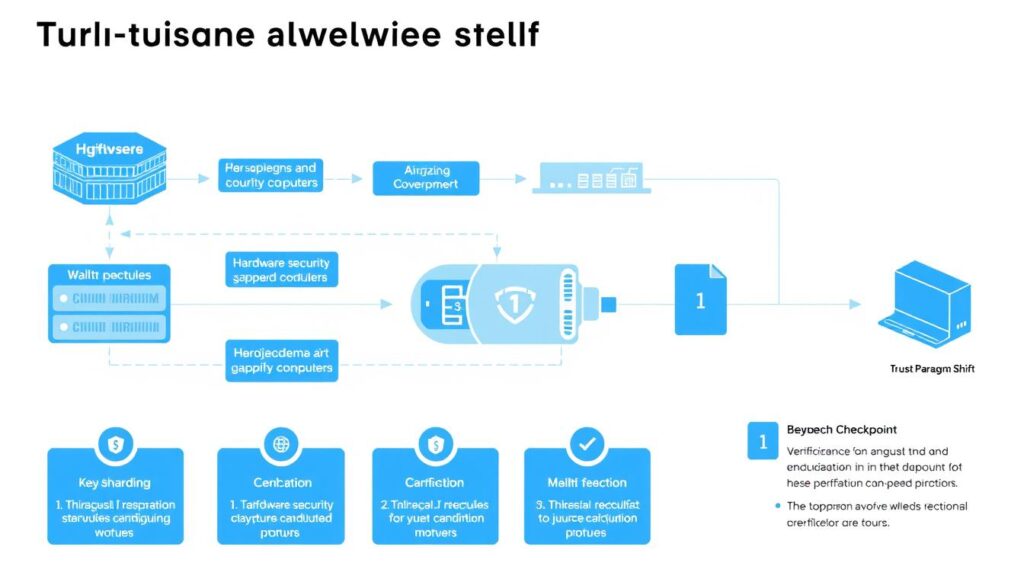
Key Open Source Technologies Enabling Institutional Custody
Multi-Signature Wallets
Multi-signature technology requires multiple keys to authorize transactions, eliminating single points of failure. Open source multi-sig implementations allow institutions to verify the security model and customize approval workflows to match their governance requirements.
Projects like Bitcoin Core provide the foundation for multi-sig capabilities, while solutions like Gordian extend these capabilities with institutional-friendly features.
Hardware Security Modules (HSMs)
Open source HSM initiatives provide tamper-resistant hardware for key storage with verifiable security properties. Unlike proprietary HSMs, open designs allow institutions to validate that no backdoors or vulnerabilities exist.
The Trussed project exemplifies this approach, creating an open framework for secure cryptographic operations that can be independently verified.

Case Studies: Open Source Custody in Action
Case Study: Unchained Capital’s Collaborative Custody
Unchained Capital has pioneered a collaborative custody model built on open source foundations. Their approach uses multi-signature technology where the institution retains control of keys while Unchained acts as a co-signer.
- Based on open source Bitcoin libraries and tools
- Transparent recovery procedures with no vendor lock-in
- Verifiable security model with published code
- Compatible with regulatory requirements for institutional investors
This model demonstrates how open source enables a trust-but-verify approach to custody, where the provider’s role is transparent and the client maintains ultimate control.
Case Study: Casa’s Key Management Protocol
Casa has developed an institutional key management solution built on open source principles. Their approach focuses on eliminating single points of failure while maintaining operational efficiency.
- Open verification of security architecture
- Geographically distributed key storage
- Role-based access controls with transparent implementation
- Emergency recovery procedures with verifiable security properties
Casa’s solution demonstrates how open source principles can be applied to create institutional-grade security without sacrificing usability or introducing hidden risks.
These practical applications show how the trust paradigm shift is moving from theory to implementation. By leveraging open source technologies, institutions can achieve both the security they require and the verifiability that builds genuine trust.
The Convergence and Future of Trust in Finance
The trust paradigm shift isn’t just affecting cryptocurrency custody—it’s beginning to influence traditional finance as well. As open source principles demonstrate their value in securing digital assets, we’re seeing a convergence where traditional institutions adopt verification-based trust models.
Growing Adoption of Open Source in Traditional Finance
Traditional financial institutions are increasingly embracing open source technologies and principles:
- Goldman Sachs released Legend, an open source data management and analysis platform
- JP Morgan developed Quorum, an enterprise-focused version of Ethereum
- The Linux Foundation hosts Hyperledger, a collaborative project with members including major banks and financial institutions
- SWIFT has explored open source approaches for financial messaging standards
This trend reflects a recognition that transparency and verification create more robust systems than proprietary, closed approaches. As digital and traditional assets increasingly coexist in institutional portfolios, open source principles provide a common foundation for security.
The Need for Global Custody Standards
As the financial world navigates this paradigm shift, establishing global standards for digital asset custody becomes crucial. These standards must bridge the gap between traditional regulatory requirements and the unique properties of blockchain-based assets.

Several initiatives are working toward this goal:
| Initiative | Focus Areas | Participants | Approach |
| Global Digital Asset Custody Standards | Key management, governance, audit | Banks, custodians, technology providers | Industry-led standardization |
| NIST Cryptographic Standards | Cryptographic algorithms, key protection | Government, academia, industry | Technical standards development |
| ISO/TC 307 | Blockchain and distributed ledger technologies | International standards bodies | Formal international standardization |
These standards will be most effective when they embrace the verification-based trust model that Bitcoin pioneered. By incorporating open source principles, they can create a framework where security doesn’t depend on blind trust but on transparent, verifiable processes.
The future of institutional custody lies at the intersection of regulatory compliance and open verification. By embracing the trust paradigm shift, institutions can build custody solutions that satisfy both regulatory requirements and the unique security needs of digital assets.
Embracing the Trust Paradigm Shift
The transition from centralized trust to verified security represents one of the most significant paradigm shifts in financial history. For institutions navigating this change, open source principles offer a path forward that combines the security required for digital assets with the transparency needed to build genuine trust.

The key takeaways for institutions approaching digital asset custody include:
- Recognize that digital assets require a fundamentally different approach to custody than traditional assets
- Embrace verification-based security rather than relying solely on trusted third parties
- Leverage open source technologies to create transparent, auditable custody solutions
- Participate in the development of standards that bridge traditional and decentralized finance
- Build internal expertise in both the technical and regulatory aspects of digital asset custody
By adopting these principles, institutions can navigate the trust paradigm shift successfully, creating custody solutions that are both secure and aligned with the unique properties of digital assets.
Future-Proof Your Custody Strategy
Ready to implement open source custody solutions for your institution? Our team of experts can help you navigate the technical, operational, and regulatory challenges.
How can institutions begin implementing open source custody solutions?
The journey typically begins with a comprehensive assessment of your current custody needs and capabilities. Start by evaluating open source solutions like multi-signature wallets and hardware security modules that align with your governance requirements. Many institutions find value in partnering with specialists who can help bridge the gap between traditional financial operations and open source security practices.
What regulatory considerations should institutions be aware of?
Regulatory requirements vary by jurisdiction, but common considerations include demonstrating adequate controls, maintaining proper segregation of duties, and implementing comprehensive audit trails. Open source solutions can actually simplify compliance by providing transparent, verifiable security processes that satisfy regulatory scrutiny. Work with legal counsel familiar with both traditional financial regulations and digital asset requirements in your jurisdiction.
How does the open source approach affect operational security?
Open source enhances operational security by eliminating security through obscurity. With transparent code and processes, vulnerabilities can be identified and addressed more quickly. However, this approach requires institutions to develop new competencies in code review, secure implementation, and ongoing monitoring. The result is typically more robust security with fewer hidden risks.

