You wouldn’t store your life savings in a shoebox under your bed. Why treat your Bitcoin any differently? As Bitcoin continues its journey toward mainstream adoption, with institutional investors entering the market and ETFs creating new demand, the need for robust security solutions has never been more critical. Single-signature wallets, while convenient, represent a significant single point of failure that could cost you everything. This comprehensive guide will transform your approach to Bitcoin security—taking you from basic wallet storage to building your own digital fortress.
What Is a Bitcoin Vault? (And What It Isn’t)
A Bitcoin vault combines multiple security layers to protect your digital assets
A Bitcoin vault is not a single product you can purchase off the shelf. Rather, it’s a strategic security framework—a combination of technology and process—designed for the long-term protection of your digital assets. At its core, a Bitcoin vault is a multi-signature, geographically distributed, and resilient system that eliminates single points of failure while providing resistance to theft, loss, and coercion.
Unlike hot wallets or exchange accounts that prioritize convenience over security, a proper Bitcoin vault implements multiple layers of protection that require specific conditions to be met before funds can be moved. This approach significantly reduces the risk profile of your Bitcoin holdings while ensuring you maintain complete sovereignty over your assets.
| Security Feature | Hot Wallet | Exchange Account | Single Hardware Wallet | Bitcoin Vault |
| Private Key Control | User-controlled | Exchange-controlled | User-controlled | Distributed control |
| Internet Exposure | Constant | Constant | Limited | Minimal to none |
| Recovery Options | Single seed phrase | Account recovery | Single seed phrase | Multiple recovery paths |
| Theft Protection | Low | Medium | Medium | High |
| Loss Protection | Low | Medium | Low | High |
| Inheritance Planning | Difficult | Limited | Difficult | Built-in |
Myth vs Reality: Many Bitcoin holders believe that simply owning a hardware wallet provides maximum security. In reality, a single hardware wallet still represents a single point of failure that can be lost, stolen, or damaged—potentially resulting in permanent loss of funds.
The Cornerstone Technology: Multi-Signature (Multi-Sig) Explained

Think of multi-signature technology like a bank safe deposit box that requires two keys to open—one held by you and one by the bank. Neither party can access the contents alone, creating a powerful security model. In the Bitcoin world, multi-signature (or multi-sig) takes this concept further by allowing you to define exactly how many keys (M) out of a total set (N) are required to authorize a transaction.
A common configuration is a 2-of-3 setup, where any two keys out of three total keys must sign a transaction. This provides an optimal balance between security and usability for most Bitcoin holders.
The Triple-Threat Protection of Multi-Sig
Protects from Theft
If an attacker gains access to one of your keys, they still cannot move your funds without additional keys. This dramatically increases the difficulty of successful theft.
Protects from Loss
If you lose access to one key, your Bitcoin remains accessible through your remaining keys. This eliminates the catastrophic risk of a single point of failure.
Enables Collaboration
Multi-sig allows you to distribute trust among multiple parties, such as family members or professional custodians, without surrendering complete control to any single entity.
Security Self-Audit: Do you currently have a backup strategy for your Bitcoin? If your primary device fails, would you still have access to your funds? Multi-signature setups address these critical vulnerabilities.
The Tools of the Trade: Hardware and Software
Hardware Selection
When building a Bitcoin vault, hardware selection is critical. You need air-gapped, single-purpose devices that minimize attack surfaces and provide robust security guarantees. The market offers several excellent options, each with unique strengths.

Top hardware wallets for multi-signature Bitcoin vaults
| Feature | Coldcard | Seedsigner | Blockstream Jade |
| Air-gapped Operation | Yes (microSD) | Yes (QR codes) | Optional (microSD/QR) |
| Open Source | Yes | Yes | Yes |
| Secure Element | Yes | No | Yes |
| Cost | $129 | $50-100 (DIY) | $49 |
| User Interface | Numeric keypad | Buttons + screen | Touchscreen |
| Security Audits | Yes | Community reviewed | Yes |
We recommend the Coldcard for its industry-leading security features, including true air-gapped operation, secure element chip, and open-source firmware that has undergone rigorous security audits. Its numeric keypad interface, while not as flashy as touchscreens, provides a robust input method that minimizes attack vectors.
Vault Coordinator Software
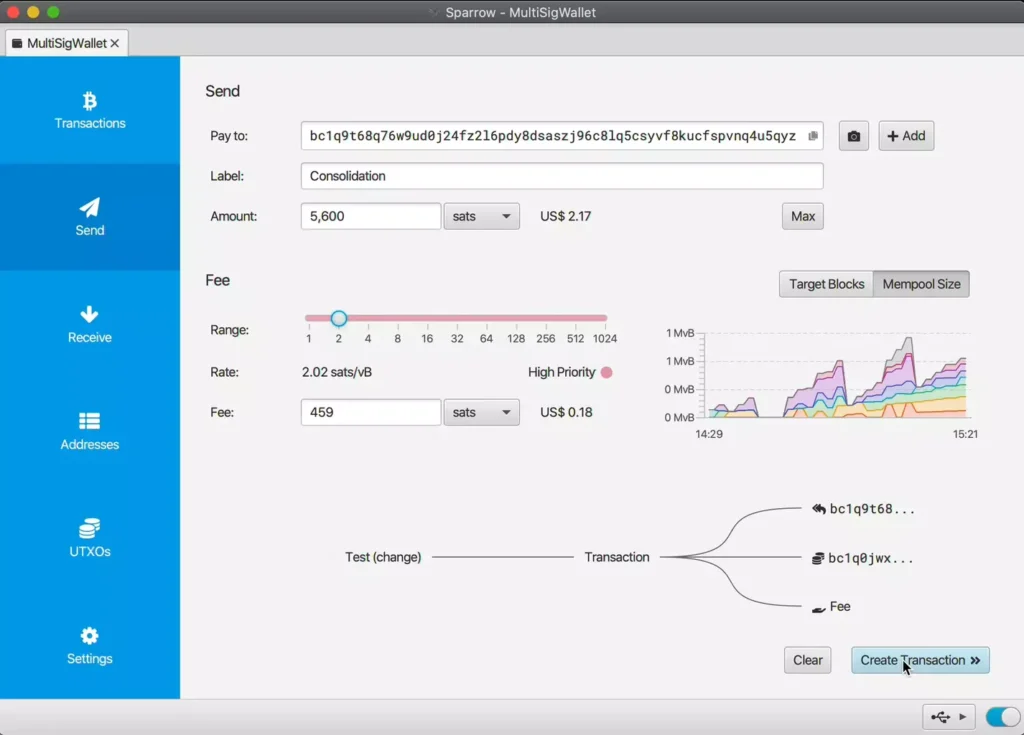
While hardware devices secure your private keys, you need specialized software to coordinate your multi-signature setup. This software creates the vault structure, manages the public keys from each device, and helps you construct and broadcast transactions when needed.
We recommend Sparrow Wallet for its powerful feature set, privacy-focused design, and transparent handling of multi-signature configurations. Sparrow provides a user-friendly interface while exposing the technical details needed to verify your setup’s security.
“The security of your Bitcoin vault is only as strong as the tools you use to build it. Open-source, audited hardware and software are non-negotiable components of a robust security strategy.”
Step-by-Step Guide: Constructing a 2-of-3 Multi-Sig Vault
1. Acquiring and Verifying Your Hardware
2. Initializing Each Hardware Device

Critical Security Note: Never generate multiple seed phrases on the same day in the same location. This reduces the risk of environmental compromises affecting all your keys simultaneously.
3. Creating the Multi-Sig Vault in Sparrow Wallet
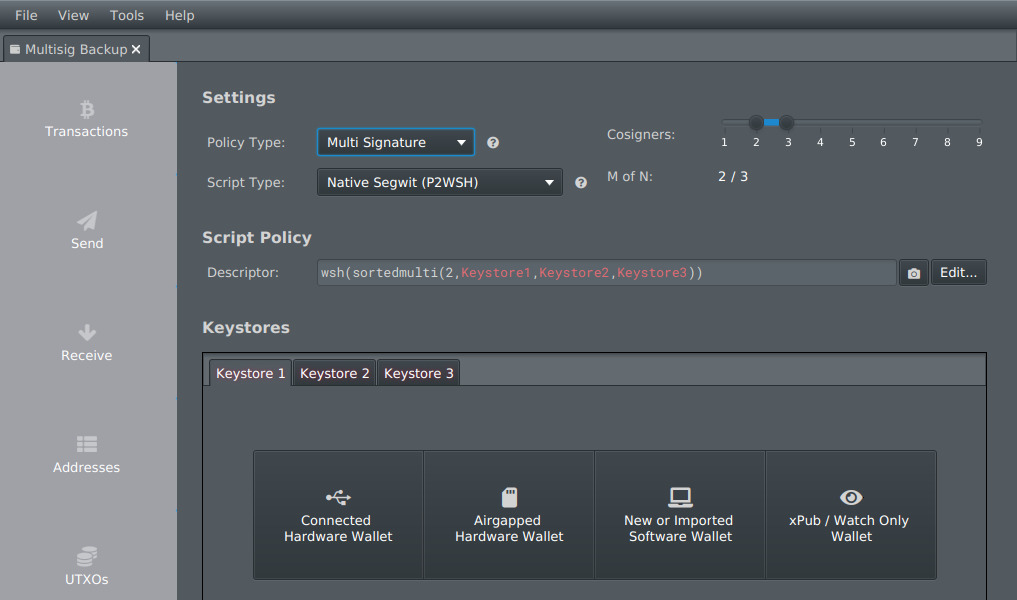
4. The Master Blueprint: Backing Up Your Wallet
The wallet output descriptor is a critical backup component that contains the public key information needed to reconstruct your vault even if you lose the coordinator software. This is separate from your seed phrases and doesn’t compromise security if stored properly.
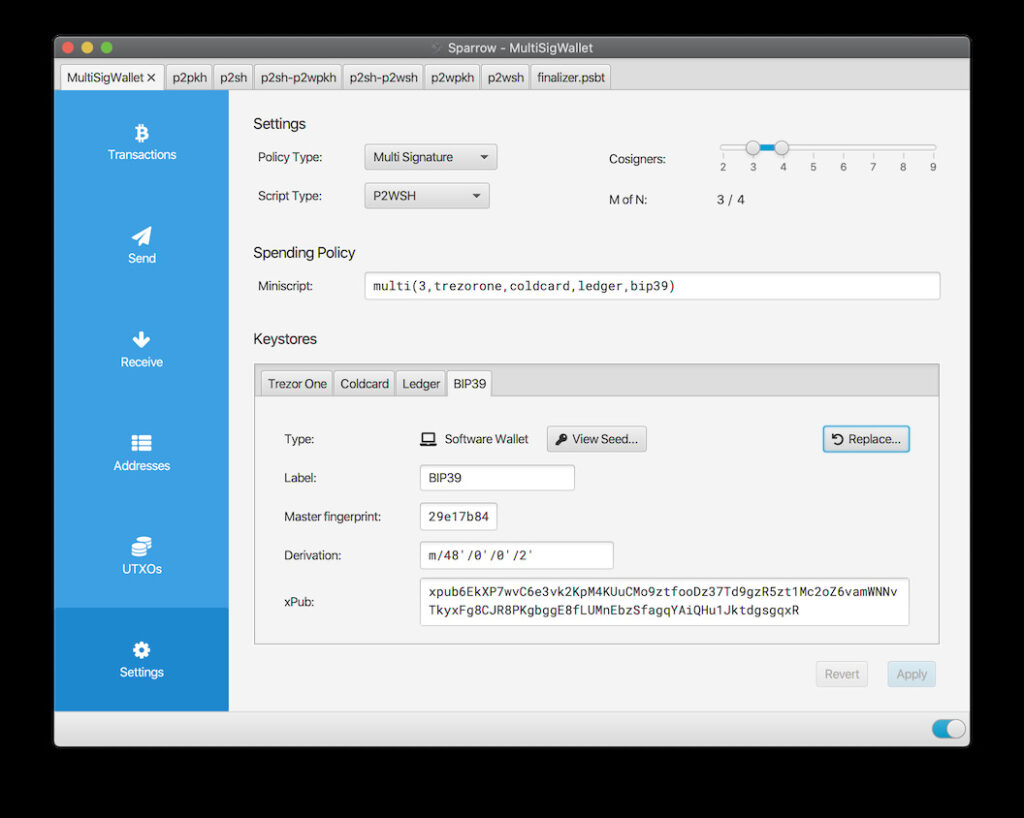
5. The Test Transaction
Before committing significant funds to your vault, it’s essential to verify the entire setup with a small test transaction. This confirms that you can both deposit and withdraw funds successfully.
Ready to build your Bitcoin vault?
Our AI-powered advisory service makes it easy to implement institutional-grade security for your digital assets.
Key Management: A Strategy for Physical Security

The technology behind your Bitcoin vault is only half the equation. Equally important is the physical security strategy you implement to protect your keys and backup materials. A comprehensive approach addresses multiple threat vectors including theft, natural disasters, and unauthorized access.
Securing Seed Phrases
Geographic Distribution
Distributing your keys and backups across multiple locations creates resilience against localized threats like fire, flood, or theft. Consider this distribution strategy for a 2-of-3 setup:
Home Location
- Device #1 with PIN protection
- Metal backup of Seed #1
- Wallet descriptor backup
- Recovery instructions
Secondary Location
- Device #2 with PIN protection
- Metal backup of Seed #2
- Wallet descriptor backup
- Recovery instructions
Secure Third Location
- Metal backup of Seed #3
- Wallet descriptor backup
- Recovery instructions
- (Device #3 optional)
Security Self-Audit: How would your current Bitcoin storage fare against a home fire? A theft? A forgotten password? Your security strategy should have clear answers for each scenario.
Threat Modeling
Effective security planning requires considering various threat scenarios and ensuring your setup addresses each one adequately.
| Threat Scenario | Vault Protection Mechanism | Action Required |
| Home fire or natural disaster | Geographic distribution of keys | Access remaining keys at alternate locations |
| Theft of one device | Multi-sig requirement (2-of-3) | None immediate; consider rotating to new keys |
| Forgotten PIN | Seed phrase backups | Restore device using seed phrase |
| Coercion attempt | Geographic distribution | Attacker cannot access all required keys |
| Lost or damaged device | Seed phrase backups | Restore to new device using seed phrase |
Collaborative Custody – Security Through Partnership

While self-custody empowers you with complete control over your Bitcoin, many users find value in a collaborative approach that combines personal sovereignty with expert assistance. This model enhances security and provides robust recovery paths without sacrificing your control over your assets.
“The most sophisticated Bitcoin security setups balance technical controls with human processes. Collaborative custody creates resilience through carefully designed trust relationships.”
Benefits of Collaborative Custody
Expert Guidance for Your Bitcoin Security
Building a robust Bitcoin vault requires technical knowledge and careful planning. Our team of security specialists can help design and implement a custom solution tailored to your specific needs.
The Final Layers: Time-Locks and Inheritance

For comprehensive long-term security and generational wealth planning, advanced Bitcoin vaults incorporate time-lock mechanisms and formal inheritance protocols. These features provide protection against sophisticated attacks and ensure your Bitcoin can be securely transferred to your heirs.
Time-Locks (CSV)
Time-locks are blockchain-enforced delays that prevent immediate movement of funds even if a vault is fully compromised. By implementing CheckSequenceVerify (CSV) in your vault design, you create a time buffer during which you can detect and respond to unauthorized access attempts.
Inheritance Planning
A complete Bitcoin security strategy must address what happens to your assets when you’re no longer able to manage them. Effective inheritance planning combines technical controls with legal documentation.
| Feature | Time-Lock Strategy | Inheritance Strategy |
| Primary Purpose | Prevent immediate theft | Enable authorized transfer to heirs |
| Implementation | Technical (CSV script) | Technical + Legal |
| Time Horizon | Days to weeks | Years to decades |
| Key Components | Delayed transactions, recovery keys | Dead man’s switch, legal documents |
| Complexity | Moderate | High |
Security Self-Audit: Have you documented a clear process for your heirs to access your Bitcoin? Would they know what to do and who to contact? If not, your inheritance planning needs attention.
From Educated to Empowered: Your Path Forward
You’ve now completed a comprehensive journey through Bitcoin vault security—from understanding the fundamental principles to exploring advanced concepts like collaborative custody and inheritance planning. With this knowledge, you’re equipped to move beyond basic wallet storage and implement institutional-grade security for your digital assets.
Remember the core principles we’ve explored:
Building your Bitcoin vault is a significant step toward true financial sovereignty. By taking control of your private keys through a thoughtfully designed security framework, you’re not just protecting your assets—you’re embracing the core principles that make Bitcoin revolutionary.
Frequently Asked Questions
How do Bitcoin vaults work?
Bitcoin vaults work by implementing multiple security layers, primarily through multi-signature technology that requires multiple private keys to authorize transactions. Unlike single-key wallets, vaults distribute trust across multiple devices and locations, eliminating single points of failure. Advanced vaults may also incorporate time-lock mechanisms that enforce waiting periods before funds can be moved, providing additional protection against theft.
How much does it cost to set up a Bitcoin vault?
The cost of setting up a Bitcoin vault varies based on your security requirements. A basic 2-of-3 multi-signature setup requires purchasing at least two hardware wallets (-0 each) and metal backup solutions for seed phrases (-0 each). The software components (Sparrow Wallet) are free and open-source. In total, expect to invest 0-0 for a robust personal vault setup, plus any additional costs for secure storage solutions.
Is a multi-signature wallet the same as a Bitcoin vault?
While multi-signature technology is a core component of Bitcoin vaults, a complete vault implementation goes beyond just multi-sig. A Bitcoin vault encompasses the entire security framework, including hardware selection, geographic distribution of keys, physical security measures, backup strategies, and inheritance planning. Multi-signature is the technical foundation, but a vault is the comprehensive security strategy built on that foundation.
Can I recover my Bitcoin if I lose one of my keys?
Yes, that’s one of the primary benefits of a multi-signature vault. In a 2-of-3 setup, you only need any two of your three keys to access your funds. If you lose one key, you can still use the remaining two to move your Bitcoin to a new vault. This resilience against key loss is a fundamental advantage over single-key wallets, where losing your only key means permanently losing access to your funds.