You’ve embraced Bitcoin’s promise of decentralization and self-sovereignty – a powerful step toward financial freedom. But with great control comes great responsibility. As you transition from ETFs to direct Bitcoin ownership, implementing robust security measures becomes not just recommended, but essential. Two-Factor Authentication (2FA) stands as your first critical defense against the unique threats facing Bitcoin holders.
In this guide, we’ll explore how 2FA works as your digital deadbolt, protecting your Bitcoin from increasingly sophisticated attacks while maintaining the simplicity needed for practical, everyday use.
Reclaiming Your Sovereignty: The Journey to Secure Bitcoin Self-Custody
Self-custody represents the true essence of Bitcoin – allowing you to hold your digital assets without relying on third parties like exchanges or ETF providers. This approach eliminates counterparty risk and aligns perfectly with Bitcoin’s founding principles of decentralization and personal sovereignty.
However, this freedom comes with responsibility. When you control your private keys, you alone are responsible for their security. Unlike traditional financial systems with fraud protection and reversible transactions, Bitcoin transactions are immutable – once executed, they cannot be reversed.
This reality makes implementing strong security practices not just good advice, but an absolute necessity. Two-Factor Authentication (2FA) serves as your first line of defense in a comprehensive security strategy.
As a Bitcoin holder embracing self-custody, your security journey begins with understanding and implementing 2FA across your entire digital ecosystem – from exchange accounts to email and beyond.
Two-Factor Authentication (2FA): Your Digital Deadbolt
What is 2FA? The Digital Deadbolt
Two-factor authentication (2FA) adds an essential extra layer of security beyond just a password. Think of it as requiring both a key AND a fingerprint to unlock your digital door. Even if someone discovers your password, they still can’t access your account without that second verification factor.
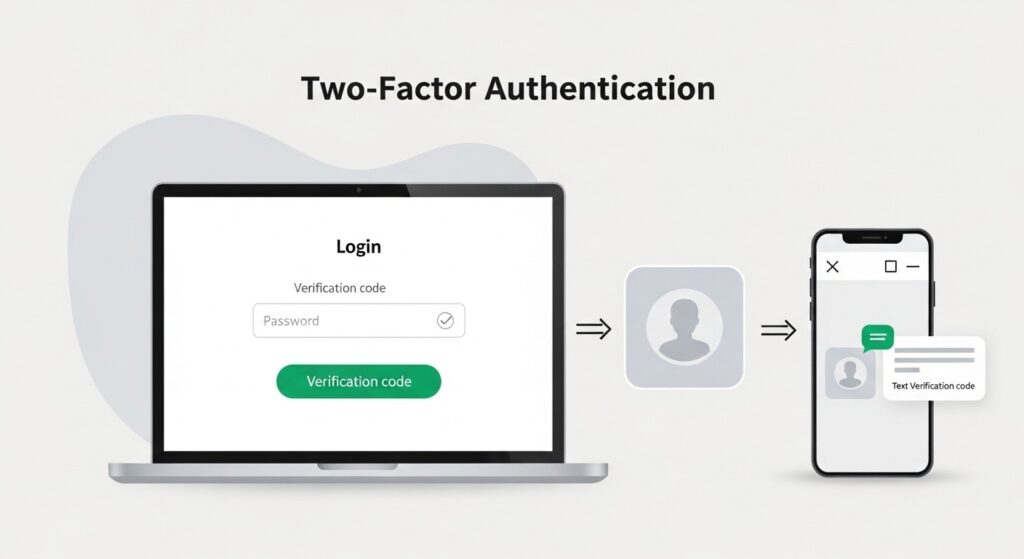
2FA works by requiring two distinct forms of verification from different categories:
- Something you know – typically your password, PIN, or security question answer
- Something you have – a physical device like your smartphone, hardware key, or authenticator app
- Something you are – biometric data like your fingerprint, face, or retina scan
When you enable 2FA on an account, you’ll first enter your username and password. Then, instead of gaining immediate access, you’ll be prompted for a second verification – typically a temporary code from your phone or a confirmation via an authenticator app.
Why 2FA is Non-Negotiable for Bitcoin Holders
For Bitcoin holders, 2FA isn’t just a good practice – it’s essential. Here’s why:
Mitigates Password Compromise
Even if your password is stolen through a data breach or phishing attack, attackers still can’t access your accounts without the second factor.
Protects Against Phishing
Sophisticated phishing attempts may trick you into revealing your password, but 2FA provides a crucial additional barrier that phishing typically can’t overcome.
Addresses the Irreversibility of Crypto
Unlike credit card transactions, Bitcoin transfers cannot be reversed. Once your coins are sent to an attacker’s wallet, they’re gone forever – making prevention absolutely critical.
Secures Your Entire Crypto Ecosystem
Your Bitcoin security is only as strong as your weakest link. 2FA helps secure not just your wallet, but your email, exchange accounts, and other services that could provide access to your assets.
Types of 2FA: Choosing Your Security Armor Wisely
Not all 2FA methods offer the same level of protection. Understanding the strengths and weaknesses of each option is crucial for Bitcoin holders seeking optimal security.
1. Authenticator Apps (Recommended for Most Digital Accounts)

Authenticator apps like Google Authenticator, Authy, and Microsoft Authenticator generate time-based, one-time passwords (TOTPs) that refresh every 30 seconds.
Advantages
- Works offline – no cell service required
- Not vulnerable to SIM swapping attacks
- Generates codes locally on your device
- Free and widely supported across services
Limitations
- Requires smartphone access
- Can be lost if phone is damaged/lost without proper backup
- Setup requires slightly more technical knowledge
When setting up an authenticator app, always save your recovery codes in a secure location! These codes are your backup access method if you lose your device.
2. Hardware Security Keys (The Gold Standard for Crypto)

Hardware security keys like YubiKey, Trezor, and Ledger (when used as U2F/FIDO devices) provide the highest level of security for your accounts.
Advantages
- Virtually phishing-proof
- Requires physical presence to authenticate
- Resistant to malware and remote attacks
- No batteries or connectivity required
- Some models work across USB, NFC, and Bluetooth
Limitations
- Costs money (typically $25-$70)
- Can be lost or damaged
- Not supported by all services
- Requires carrying a physical device
3. SMS and Voice Verification (Not Recommended for Crypto)

Warning: SMS-based verification is vulnerable to SIM swapping attacks and should be avoided for securing Bitcoin-related accounts whenever possible.
SMS verification sends a one-time code to your phone number via text message. While better than no 2FA at all, this method has significant vulnerabilities that make it unsuitable for high-value Bitcoin accounts.
Advantages
- Widely supported across services
- Familiar and easy to use
- Works on any mobile phone (not just smartphones)
Limitations
- Vulnerable to SIM swapping attacks
- Can be intercepted by sophisticated attackers
- Requires cell service to receive codes
- Not secure for high-value accounts
What is a SIM Swapping Attack?
SIM swapping occurs when an attacker convinces your mobile carrier to transfer your phone number to their device. Once successful, they receive all your SMS messages, including 2FA codes, allowing them to bypass this security measure.
Where to Implement 2FA: Securing Your Bitcoin Ecosystem
Effective security requires protecting your entire digital ecosystem, not just your Bitcoin wallet. Here are the critical places to implement 2FA:

Cryptocurrency Exchanges
Even if you primarily self-custody, you likely still use exchanges occasionally. These are prime targets for attackers due to the potential value they hold.
Priority: Critical
Email Accounts
Your email is often the master key to all your other accounts through password resets. If an attacker controls your email, they can potentially access everything else.
Priority: Critical
Cloud Storage
If you store wallet backups, seed phrases, or other sensitive information in cloud storage, these accounts must be secured with strong 2FA.
Priority: Critical
Password Managers
Your password manager contains the keys to your digital kingdom. Protecting it with 2FA is essential for maintaining the security of all your accounts.
Priority: High
Social Media Accounts
Compromised social accounts can be used for reputation attacks or to phish your contacts. They also often contain personal information useful for targeted attacks.
Priority: Medium
Phone and Device Accounts
Your Apple ID, Google account, and similar services control access to your devices and often contain payment information and personal data.
Priority: High
Setting Up 2FA: A Step-by-Step Guide
Implementing 2FA doesn’t have to be complicated. Follow these general steps to secure your accounts:
-
Choose your 2FA method
For Bitcoin-related accounts, we recommend using an authenticator app or hardware security key. Avoid SMS verification when possible.
-
Download an authenticator app (if using)
Google Authenticator, Authy, and Microsoft Authenticator are all excellent options. Consider Authy if you want built-in backup capabilities.
-
Access your account security settings
Look for “Security,” “Privacy,” or “Account” sections in the service you want to protect. Find the 2FA or two-step verification option.
-
Follow the setup process
Typically, you’ll scan a QR code with your authenticator app or connect your hardware key when prompted.
-
Save your recovery codes
This critical step is often overlooked! Store these codes securely offline – they’re your backup if you lose access to your 2FA device.
-
Test the login process
Log out and back in to ensure everything works correctly before moving on.
-
Repeat for all critical accounts
Prioritize exchanges, email, and financial services first, then secure other accounts.
When setting up 2FA on multiple accounts, consider creating a secure inventory of which authentication method you’ve used for each service. This prevents confusion and lockouts later.
2FA Best Practices for Bitcoin Holders
Maximize your security by following these essential best practices:
Use Multiple Authentication Methods
Don’t rely on just one 2FA method. For critical accounts, consider using both an authenticator app AND a hardware security key when supported. This provides redundancy if one method becomes unavailable.
Backup Your Authentication Methods
Always save recovery codes in a secure, offline location. Consider using a fireproof safe or safety deposit box for critical backups. If using Authy, enable encrypted backups with a strong password.
Avoid SMS When Possible
While SMS verification is better than no 2FA at all, it should be your last choice due to SIM swapping vulnerabilities. Use it only when no other options are available.
Regularly Audit Your Security
Set a calendar reminder to review your security setup quarterly. Check which accounts have 2FA enabled, test your recovery methods, and update as needed.
Use Different 2FA Apps for Critical Accounts
Consider using separate authenticator apps for your most critical accounts (like exchanges) versus general accounts. This creates isolation that can prevent total compromise.
Be Wary of Account Recovery Options
Some services offer alternative recovery methods that can bypass 2FA. Review these carefully and disable any that could create security vulnerabilities.
Overcoming Common 2FA Challenges
While 2FA significantly enhances your security, it can present some challenges. Here’s how to address them:

What if I lose my phone or authentication device?
This is why recovery codes are critical. Store these codes securely offline. For authenticator apps like Authy, you can enable multi-device support with encrypted backups. For hardware keys, always have a backup key stored in a secure location.
What if a service doesn’t support my preferred 2FA method?
Use the strongest method available. If only SMS is offered, it’s still better than no 2FA at all. Consider requesting stronger 2FA options from the service provider or evaluating alternative services that offer better security.
How do I handle 2FA when traveling?
Ensure your authenticator apps are accessible offline. For hardware keys, consider bringing a backup stored separately from your primary key. If using SMS verification, check that your phone plan includes international service or set up alternative verification methods before traveling.
What if I’m locked out of my account despite having 2FA?
Each service has its own account recovery process. This typically involves verifying your identity through alternative means or using your saved recovery codes. For critical accounts, familiarize yourself with the recovery process before you need it.
Beyond 2FA: Building Your Complete Security Fortress
While 2FA is essential, it’s just one component of a comprehensive security strategy for Bitcoin self-custody. Here’s what else to consider:
Hardware Wallets
Physical devices specifically designed to secure cryptocurrency private keys. They keep your keys offline and require physical confirmation for transactions.
Secure Password Management
Use a reputable password manager to generate and store strong, unique passwords for all your accounts.
Proper Seed Phrase Storage
Secure your wallet recovery phrases using appropriate methods like metal backups, multiple locations, and potential multisig setups.
Network Security
Use VPNs, secure your home network, and be cautious on public Wi-Fi to prevent network-based attacks.
Device Security
Keep all devices updated, use antivirus protection, and consider dedicated devices for cryptocurrency management.
Operational Security
Be mindful of what you share online, who knows about your holdings, and how you discuss your Bitcoin investments.
Ready to Take Your Bitcoin Security to the Next Level?
Join our educational platform for comprehensive guides on all aspects of Bitcoin self-custody security – from basic setup to advanced multisig configurations.
Conclusion: Your Journey to Secure Bitcoin Self-Custody

Implementing Two-Factor Authentication (2FA) is your first crucial step toward robust Bitcoin security. By adding this additional layer of protection to your accounts, you significantly reduce the risk of unauthorized access and potential loss of your digital assets.
Remember that security is not a one-time setup but an ongoing process. Regularly review your security practices, stay informed about emerging threats, and continue to build your knowledge of Bitcoin self-custody best practices.
By taking control of your Bitcoin security today, you’re not just protecting your assets – you’re embracing the true ethos of Bitcoin: financial sovereignty, personal responsibility, and freedom from third-party control.

